Today, it is undeniable that information has become a valuable asset for companies of all sizes. With the rapid evolution of technology, information security is a crucial topic to guarantee the integrity, confidentiality and availability of business data.
In this era where connectivity is the backbone of business, protecting information from cyber threats is more vital than ever. And no wonder: according to a study by the University of Maryland , hackers attack every 39 seconds around the world , on average.
Therefore, in this article, we will delve into the world of information security, explaining what it means for business and highlighting the importance of keeping business data secure.
Throughout the text, we will explore the most common threats organizations face today, providing insights into how entrepreneurs and managers can implement effective security practices to protect their digital assets.
Stay with us!
What is information security?
Information security is about the set of practices and tools designed to protect data and systems against improper access or attacks, ensuring the confidentiality, integrity and availability of information.
Encompassing measures such as encryption, access control and security strategies to safeguard sensitive information, this data protection is built around three fundamental pillars known as the CIA Triad : confidentiality , integrity and availability .
Confidentiality ensures that only authorized people have access to certain information . Integrity refers to the accuracy and completeness of data, preventing unauthorized changes . On the other hand, availability ensures that information is accessible to authorized users whenever necessary.
Why is information security crucial for companies?
Business data, which includes sensitive information, business strategies and confidential customer data, represents crucial assets that, if compromised, could result in serious financial, reputational and legal consequences.
Thus, information security not only protects against potential financial losses, but also preserves trust while maintaining brand integrity.
See below some key items of this process:
- Confidentiality : prevents confidential data from being accessed by unauthorized individuals, maintaining the privacy of the information;
- Integrity: ensures that information is not altered inappropriately, intentionally or accidentally;
- Authenticity: ensures that the parties involved in a transaction or communication are in fact who they claim to be;
- Availability: Seeks to ensure that data is available for legitimate access and use whenever necessary.
Companies that fail to maintain the security of their information can suffer severe impacts, ranging from significant financial losses to legal action for regulatory violations, such as those stipulated by the General Data Protection Law in Brazil.
What are the main impacts of a security incident?
Security incidents go beyond data loss and can include theft , damage and vulnerabilities exploited by cyber criminals, resulting in material and immaterial losses.
A data breach, for example, can result in the unauthorized disclosure of sensitive and confidential information, resulting in high repair costs, regulatory fines and image recovery, as consumer trust is compromised.
Therefore, IT security are essential in preventing attacks and promoting a strong digital security culture.
What are the most common threats to information security?

Currently, companies and organizations face constant challenges due to the various forms of cyber attacks carried out by criminals. Among the most common threats are malware , phishing , and social engineering attacks , each posing specific risks to businesses and users.
See details below:
Malware
Malware, a term that combines the words “ malicious ” and “ software ,” refers to programs designed to infect and damage systems . Types of malware include viruses, ransomware , and spyware . Ransomware it blocks access to the system or data until a ransom is paid. Spyware hand , can secretly monitor and transmit user activities.
phishing
This is an online fraud technique where criminals send emails or messages that appear to be from reliable sources, but aim to obtain sensitive information such as logins and bank details. Phishing messages often trick the recipient into clicking on malicious links, leading to data loss or security breaches.
Social engineering attacks
Such attacks manipulate individuals into revealing confidential information or taking actions that compromise information security. They exploit human trust and often precede other forms of digital attacks, paving the way for more direct threats to the information system.
What are the existing rules and regulations?
Information security regulations exist in Brazil and around the world and aim to protect data and ensure the integrity, confidentiality and availability of information. Therefore, they are essential to combat cybercrime, ensuring legal compliance and risk management.
Let's look at some:
GDPR (General Data Protection Regulation)
The GDPR is a European Union that establishes guidelines for the collection and processing of personal information of EU citizens. This regulation requires companies to implement appropriate technical and organizational measures to ensure an appropriate level of security, including protection against unauthorized access and data leaks.
LGPD (General Data Protection Law) in Brazil
In Brazil, the LGPD regulates the processing of personal data, including in digital media, by natural or legal persons governed by public or private law. The law was influenced by the GDPR and aims to ensure the privacy and protection of personal data, through a set of governance and compliance practices.
ISO 27001 – Information Security Management System
ISO 27001 provides requirements for an information security management system (ISMS) , enabling organizations to manage the security of assets such as financial information, intellectual property, employee details or information entrusted by third parties. Adherence to this standard is essential to establish, implement, operate, monitor, review, maintain and improve information security.
Information security: how to protect your business data
To ensure that a company's data is well protected, it is essential to adopt a set of strategic measures ranging from internal policies to advanced technologies. The focus needs to be on protection, prevention and responsiveness to incidents.
Check out:
Security Policies
Security policies are fundamental to establishing the standards and procedures to be followed by everyone in the company. They help prevent leaks and improper access to corporate data. For example, defining rules for creating strong passwords and regulating access to sensitive information are common practices in efficient security policies.
Education and training
Investing in employee education and training is essential, as the human factor can be one of the biggest risks to information security. Thus, awareness programs and courses on data security help create a corporate culture of vigilance and protection.
Monitoring and auditing
A proactive approach to information security involves constant monitoring and auditing of the company's systems. This includes using tools that detect and alert about suspicious activity, facilitating rapid intervention to protect business data.
Security technologies
In the technological field, the implementation of security technologies such as firewalls and antivirus software is essential. Other features such as encryption strengthen the company's network security, ensuring that, even in the event of possible interception, data is inaccessible to unauthorized third parties.
See below for details about some of these technologies:
Firewall and IDS/IDP
Firewalls and intrusion detection and prevention systems (IDS/IPS) are essential elements in company information security. A firewall acts as a barrier between a secure internal network and untrusted networks, inspecting incoming and outgoing traffic and blocking or allowing data based on a defined set of security rules.
On the other hand, an IDS monitors network traffic for suspicious activity that could indicate an intrusion attempt, while an IPS, which is a step forward from IDS, not only detects but also attempts to prevent the identified malicious activity.
Antivirus and antimalware
These are software designed to protect computers and networks against viruses, worms , Trojans and spyware . They work by scanning the system for known malware and suspicious behavior, removing or quarantining detected threats to prevent them from causing harm.
Additionally, many modern antivirus and antimalware solutions also include real-time such as heuristic scans and automatic updates to constantly adapt to new threats that are emerging.
Network security
Covers all policies, procedures and practices adopted to prevent and monitor unauthorized access, misuse, modification or denial of a computer network and network-accessible resources.
This includes a variety of technologies, devices and processes, such as the aforementioned firewalls , IDS/IPS, antivirus, encryption, access control and vulnerability management. Network security aims to ensure the integrity, confidentiality and availability of network data and services.
Why are access and identity controls important?
The implementation of access and identity controls is essential to strengthen information security. They ensure that critical resources are protected from unauthorized access, while allowing legitimate users to have the authentication and authorization to perform their activities securely.
Check out details about access and identity controls below:
User authentication
Authentication is the process of verifying that someone is who they say they are . In an information security context, it is essential to ensure that access passwords and other credentials are assigned and used correctly.
Therefore, robust authentication methods protect against intrusion by confirming the user's identity through one or more forms of validation, such as something the person knows (a password), something the person has (a token), or something the person knows (a password). person is (biometrics).
Authorization and privilege control
After authentication, authorization defines what a user can do within a system, what resources they can access, and the actions they can perform.
Privilege control is an intrinsic part of this process, determining each individual's level of access to protect privacy and prevent excesses that could lead to security breaches. Privilege management ensures that users do not have more access than necessary, adopting the principle of least privilege.
Identity management
Identity management facilitates the creation , maintenance and removal of access to systems and applications. This management process involves monitoring the life cycle of user identities.
Furthermore, it integrates different technologies and platforms so that access control is efficient and secure. It is an essential component to ensure consistency in information security strategies and minimize the risks associated with it.
Information security on mobile devices
We live in an era where different mobile devices are increasingly appearing to make our personal and professional lives easier. However, information security on these devices is essential to protect sensitive data and systems from digital threats.
Therefore, with the increasing use of notebooks, smartphones and tablets for remote work, specific measures are necessary to guarantee the integrity and confidentiality of business information. See some of them:
Mobile security policies
To protect mobile devices, it is essential to implement well-defined security policies. These policies should cover mandatory installation of security updates , use of protective software , and encryption of hard drives. Furthermore, it is important to carry out periodic training with users to ensure that they are aware of the risks and best practices in handling their devices.
VPNs and secure connections
Using a VPN ( Virtual Private Network ) is extremely important for maintaining secure connections, especially on public networks. A VPN creates an encryption-protected tunnel , ensuring that data in transit between mobile devices and company servers remains inaccessible to malicious interception. It is recommended to opt for VPNs recognized on the market that offer a high level of security.
Risks associated with remote work
With the COVID-19 pandemic, remote work was consolidated and brought with it specific risks such as access to insecure Wi-Fi networks and the possibility of theft or physical loss of devices. The adoption of tools that enable tracking and remote removal of information in cases where a mobile device is lost is an extra layer of security to protect systems and data security. Furthermore, the use of multi-factor authentication is recommended to access corporate information.
How to manage security incidents efficiently
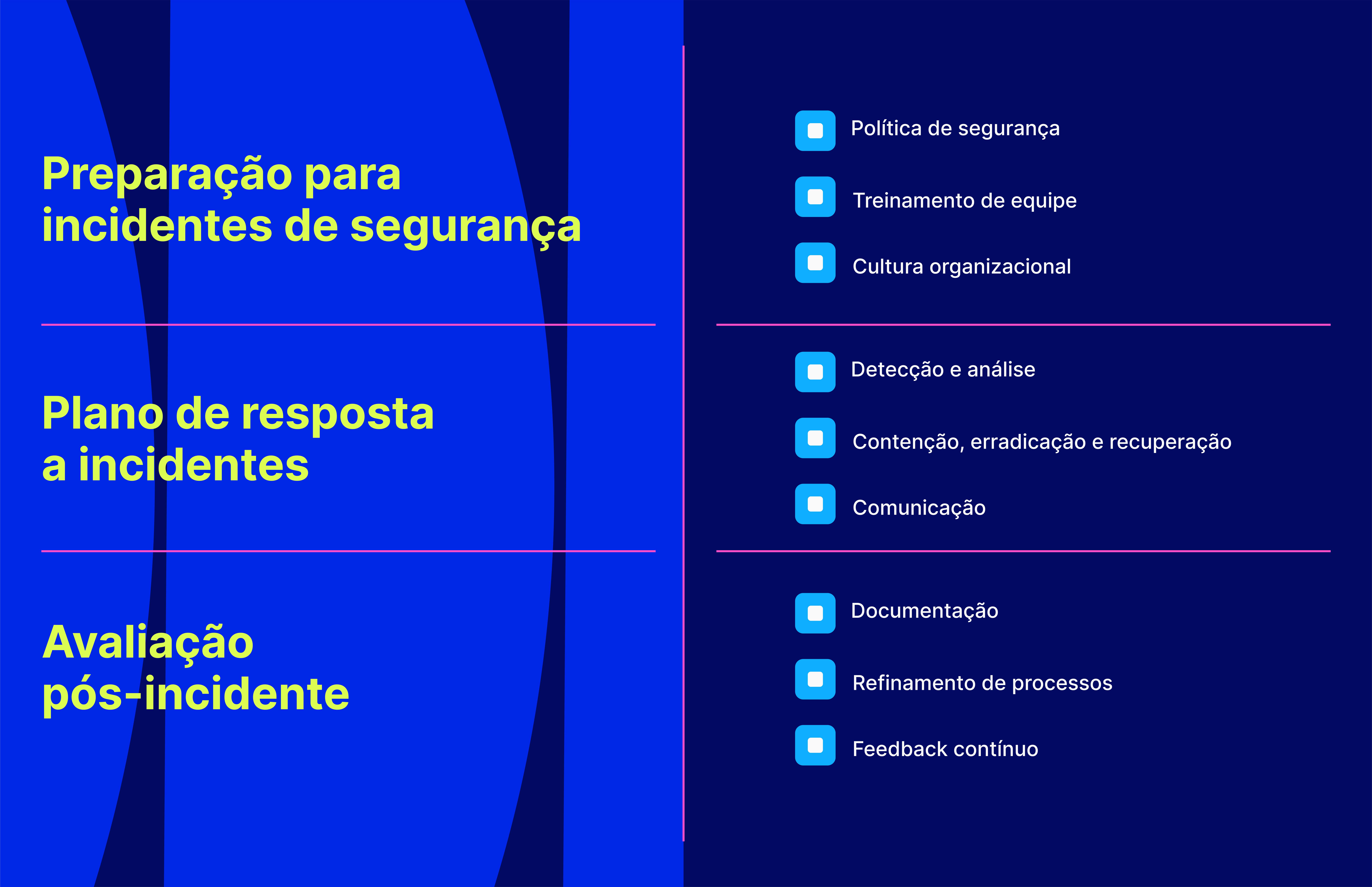
To ensure the integrity of processes and the reliability of information, having effective security incident management in your company is essential.
This involves preparation, a well-structured incident response plan, and a solid post-incident assessment, always aligning with compliance . Check out each step below:
Preparing for security incidents
Preparation is the cornerstone of information security incident management. Organizations must establish a clear policy , define and train a dedicated team and ingrain a culture of safety among employees. Additionally, it is important to conduct periodic risk audits and develop detailed contingency strategies for various scenarios.
- Security Policy: define standards and procedures;
- Team Training: train people to respond quickly and efficiently;
- Organizational Culture: promote awareness of information security.
Incident response plan
A robust incident response plan is needed to efficiently deal with threats. Specific actions for incident detection, containment, eradication and recovery must be It is essential to clarify the roles and responsibilities of each team member during an incident, ensuring coordinated and effective execution.
- Detection and Analysis: monitoring systems for rapid identification of threats;
- Containment, Eradication and Recovery: procedures to neutralize incidents and resume normal operations;
- Communication: internal and external communication strategies.
Post-incident assessment
After resolving an incident, it is essential to carry out an assessment to identify the causes and improve future processes . This assessment must document what happened, analyze the team's performance and recommend actions to reinforce security. Learning from each incident is vital to improving security strategies and increasing organizational resilience against future threats.
- Documentation: record the incident and the response given in detail;
- Process Refinement: adjust the incident response plan based on case analysis;
- Feedback : encourage feedback for continuous improvement of security practices.
What to expect from the future of information security?
Information security is constantly evolving, and some of the biggest changes are driven by emerging technologies . The future involves proactive strategies and the use of advanced tools to combat cyber threats.
Discover more details about this future below:
Machine Learning and AI
Artificial Intelligence (AI) and Machine Learning are becoming essential in detecting and responding to security incidents. They enable behavioral analysis to identify suspicious activity and automate responses to threats, improving information security efficiency. The ability to process large volumes of data and learn from it makes it easier to identify attack patterns.
Internet of Things (IoT)
With the rise of the Internet of Things (IoT), more devices are connected to the internet, and each represents a potential entry point for attackers. The expansion of IoT requires information security strategies to be robust and capable of protecting a large amount of devices and data. Thus, IoT brings challenges in terms of scale and complexity, requiring cybersecurity to be an intrinsic part of device design.
cloud security
This is a critical component of digital transformation and its role is increasingly centralized. With the increasing use of cloud-based services, it is necessary to implement specific measures that ensure the protection of data and applications in this environment. Protecting data in transit and at rest, access management and the security of interfaces and APIs are vital aspects of ensuring information security in the cloud.
Protect your business with Skyone
Now that you know that digital threats are constantly evolving , cybersecurity is not just an option, but a vital necessity for protecting your data and ensuring the continuity of your business.
We, at Skyone , position ourselves as a strategic ally to strengthen your company's security. Through a proactive approach, our platform offers specialized cybersecurity solutions designed to take action against a wide range of digital threats.
Don't wait until it's too late. Discover our platform today and take the next step towards robust and reliable cybersecurity!
Conclusion
Throughout this article, we explore the multiple aspects and crucial importance of information security in the business context. This security is not a simple line of defense, but rather a complex structure that encompasses management practices, advanced technologies and a robust organizational culture focused on data protection.
In this context, have you ever heard of Pentest (or penetration testing) ? This is an essential tool for any business that needs to evolve in cybersecurity and increasingly arm itself against threats.





